Virtual Private Gateway
Outbound Filter
The VPG Outbound Filter option allows you to specify a whitelist or blacklist of IP address ranges where outgoing traffic can or cannot be routed, and in turn ensure that your devices are not allowed to access unauthorized resources. Outbound Filter can be applied to VPGs with Canal, Door, and Direct (using the direct route to your private network environment through VPC Peering Connections, VPN connections, or virtual interfaces), as well as VPGs where the Internet gateway is enabled.
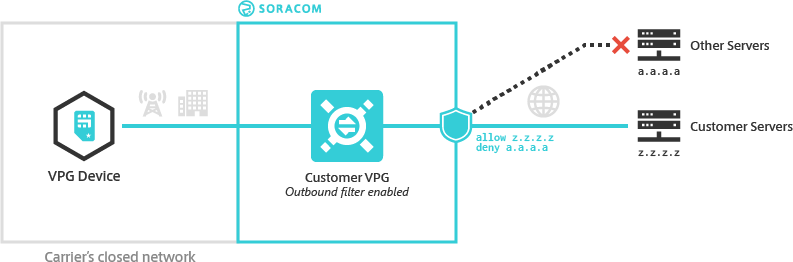
By applying an Outbound Filter to your VPG, you can effectively prevent devices from communicating with untrusted servers, or protect data from being sent to unknown destinations.
Filter Rules
An Outbound Filter consists of one or more rules, with each rule containing the following parameters:
- Action - Either
allowordeny, depending on whether traffic matching this rule should or should not be routed - IP Address Range - A CIDR block that defines a range of IP addresses
When a rule action set to allow, any traffic where the destination IP address matches the IP address range will be permitted. Similarly, if the action is set to deny, then the traffic will be blocked.
If rules contain overlapping IP address ranges, the action for the CIDR block with the larger mask (or more specific IP address range) will be used for the filter behavior. For example, if a filter:
- Allows traffic to
192.0.2.128/25(25 mask bits, 128 IP addresses from192.0.2.128to192.0.2.255) - Denies traffic to
192.0.2.128/28(28 mask bits, 16 IP addresses from192.0.2.128to192.0.2.143)
Then any traffic bound for 192.0.2.130 will be matched with the second rule 192.0.2.128/28 and the traffic will not be routed.
Configuration
You can configure a VPG's outbound filter rules from the User Console.
-
Login to the User Console. From the Menu, open the VPG screen.
-
From the list of VPGs, click the name of the VPG you want to configure to open its settings page.
-
Click the Access control tab.
-
To deny access to the internet, from the VPG routing outbound filter panel, check Block route to the internet. Selecting this option will automatically create a rule to
denyall traffic to0.0.0.0/0, effectively blocking all internet access. Alternatively, if you require more granular control, you can manually add outbound filter rules. To do this, see the instructions in the next step.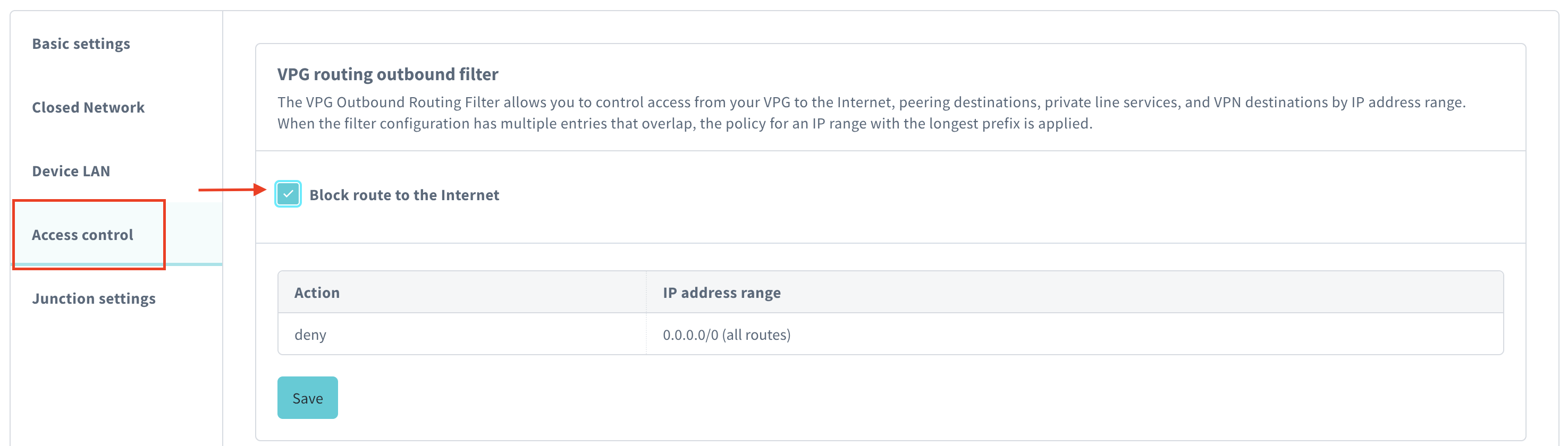
-
To add or modify rules manually, uncheck the checkbox labeled Block route to the internet and click the Add button from the VPG routing outbound filter panel.
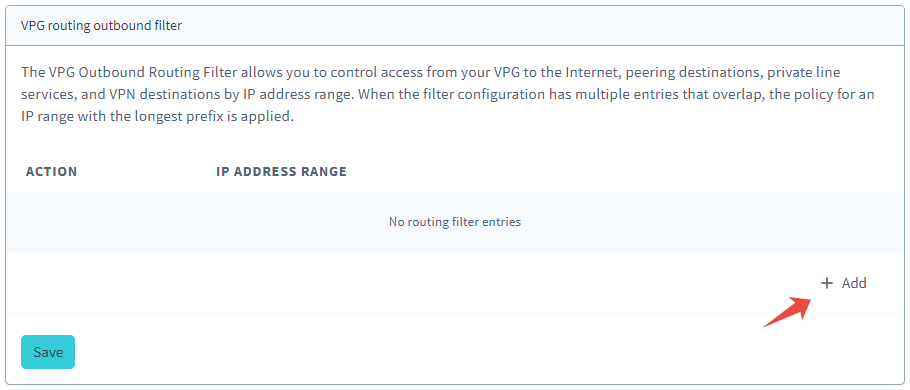
-
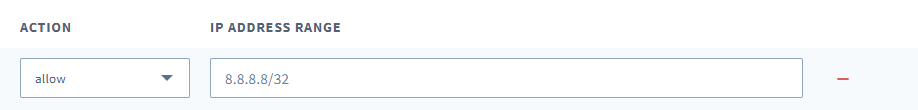
Enter the rule (
allowordeny) under Action and enter the IP address range. - Repeat steps 5 and 6 for any additional rules.
-
Click Save to finalize the outbound filter creation.
Limitations
The Outbound Routing Filter cannot prevent communications to the following Soracom endpoints:
- Soracom Beam -
beam.soracom.io. - Soracom Funnel -
funnel.soracom.io. - Soracom Funk -
funk.soracom.io. - Soracom Harvest Data/Files -
harvest.soracom.ioandharvest-files.soracom.io. - Unified Endpoint -
uni.soracom.ioorunified.soracom.io. - Ping Response Service -
pong.soracom.io. - Soracom Air Metadata Service -
metadata.soracom.io. - Soracom's DNS Servers -
100.127.0.53and100.127.1.53. - Soracom's NTP Server -
ntp.soracom.io.
When using Soracom Gate it is not possible to filter communications from the Gate Peer server to SIMs that belong to the VPG.
Programmatic Usage
You can use the Soracom API and Soracom CLI to configure Outbound Filter rules programmatically. Each rule should contain the following parameters:
- action (string, required) - Either
allowordeny, depending on whether traffic matching this rule should or should not be routed - ipRange (string, required) - A CIDR block that defines a range of IP addresses
For example, the following filter will prevent any devices attached to the VPG from communicating with a network resource in the 192.0.2.0/26 IP address range:
[
{
"action": "deny",
"ipRange": "192.0.2.0/26"
}
]You can combine multiple rules to define additional routing behavior. For example, the following filter will allow traffic to be routed to destinations within the 192.0.2.128/25 IP address range, while preventing traffic from being routed to any other destination:
[
{
"action": "deny",
"ipRange": "0.0.0.0/0"
},
{
"action": "allow",
"ipRange": "192.0.2.128/25"
}
]Then, simply pass in the filter configuration to the Soracom API or Soracom CLI. For either method, you will need the VPG ID.
Soracom API
To access the Soracom API, first use the auth API to obtain an API Key and Token. Refer to the API Usage Guide for instructions on how to use the API Key and Token in API requests.
Then, use the setRoutingFilter API to set the Outbound Filter rules:
curl -X GET \
| -H 'X-Soracom-API-Key: <MY-API-KEY>' \
| -H 'X-Soracom-Token: <MY-TOKEN>' \
| -H 'Content-Type: application/json' \
| -d '[
| {
| "action": "deny",
| "ipRange": "0.0.0.0/0"
| },
| {
| "action": "allow",
| "ipRange": "10.0.0.123/32"
| }
| ]' \
| https://g.api.soracom.io/v1/virtual_private_gateways/<VPG-ID>/set_routing_filterSoracom CLI
To use the Soracom CLI, you must first configure it to authenticate with your account information, authorization key, or SAM user credentials.
Then, run the following command to set the Outbound Filter rules:
soracom vpg set-routing-filter --vpg-id '<VPG-ID>' --body '@path/to/filter.json' --coverage-type gIn this sample, we're using the @filename method for passing in the filter definition which is stored in a separate file, but you can of course pass the raw data into the --body parameter directly.